RKHunter是一款专业的检测系统是否感染rootkit工具,RKHunter可以通过执行一系列的脚本来确认服务器是否已经感染rootkit。本文主要为大家介绍RKHunter安装及使用教程,供大家参考。
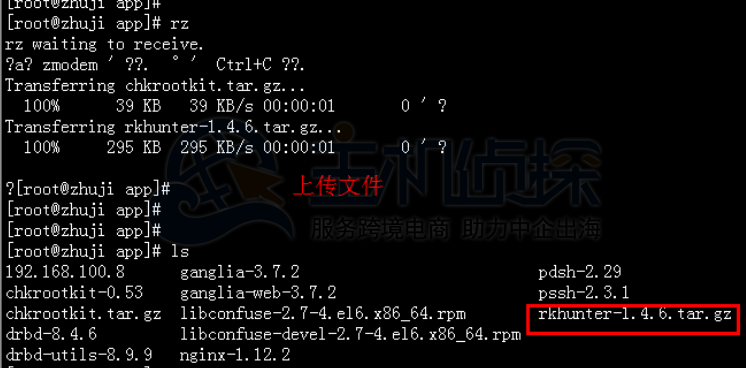
1、安装RKHunter(下载地址:https://sourceforge.net/projects/rkhunter/files/latest/download)
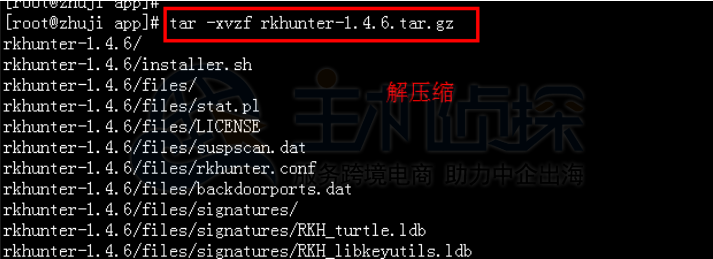
[root@server ~]# tar -zxf rkhunter-1.4.6.tar.gz #版本可能不同,命令都一样
[root@server ~]# cd rkhunter-1.4.6
[root@server rkhunter-1.4.6]# ./installer.sh –layout default –install
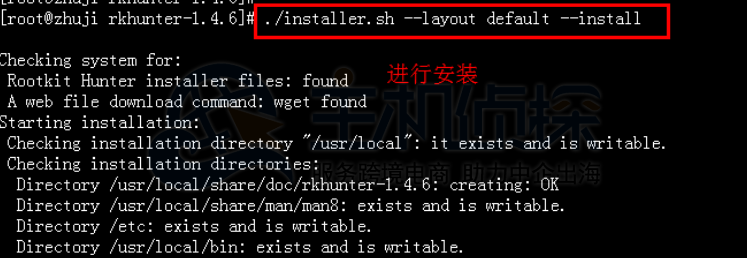
注意:RKHunter的默认安装方式,目录:/usr/local/bin
2、RKHunter常用参数列表
| 参数 | 含义 |
| -c, –check | 必选参数,表示检测当前系统 |
| –configfile <file> | 使用特定配置文件 |
| –cronjob | 作为cron任务定期运行 |
| –sk, –skip-keypress | 自动完成所有检测,跳过键盘输入 |
| –summary | 显示检测结果的统计信息 |
| –update | 检测更新内容 |
| -V, –version | 显示版本信息 |
| –versioncheck | 检测最新版本 |
| –propupd [file | directory ] | 建立样本文件,建议安装完系统就建立 |
检测示例:
[root@master rkhunter-1.4.6]# rkhunter -c
[ Rootkit Hunter version 1.4.6 ]
Checking system commands...
Performing 'strings' command checks
Checking 'strings' command [ OK ]
Performing 'shared libraries' checks
Checking for preloading variables [ None found ]
Checking for preloaded libraries [ None found ]
Checking LD_LIBRARY_PATH variable [ Not found ]
Performing file properties checks
Checking for prerequisites [ Warning ]
/usr/local/bin/rkhunter [ OK ]
/usr/sbin/adduser [ OK ]
/usr/sbin/chkconfig [ OK ]
/usr/sbin/chroot [ OK ]
/usr/sbin/depmod [ OK ]
/usr/sbin/fsck [ OK ]
/usr/sbin/groupadd [ OK ]
/usr/sbin/groupdel [ OK ]
/usr/sbin/groupmod [ OK ]
/usr/sbin/grpck [ OK ]
/usr/sbin/ifconfig [ OK ]
/usr/sbin/ifdown [ Warning ]
/usr/sbin/ifup [ Warning ]
/usr/sbin/init [ OK ]
/usr/sbin/insmod [ OK ]
/usr/sbin/ip [ OK ]
/usr/sbin/lsmod [ OK ]
/usr/sbin/lsof [ OK ]
/usr/sbin/modinfo [ OK ]
/usr/sbin/modprobe [ OK ]
/usr/sbin/nologin [ OK ]
/usr/sbin/pwck [ OK ]
/usr/sbin/rmmod [ OK ]
/usr/sbin/route [ OK ]
/usr/sbin/rsyslogd [ OK ]
/usr/sbin/runlevel [ OK ]
/usr/sbin/sestatus [ OK ]
/usr/sbin/sshd [ OK ]
/usr/sbin/sulogin [ OK ]
/usr/sbin/sysctl [ OK ]
/usr/sbin/useradd [ OK ]
/usr/sbin/userdel [ OK ]
/usr/sbin/usermod [ OK ]
/usr/sbin/vipw [ OK ]
/usr/bin/awk [ OK ]
/usr/bin/basename [ OK ]
/usr/bin/bash [ OK ]
/usr/bin/cat [ OK ]
/usr/bin/chattr [ OK ]
/usr/bin/chmod [ OK ]
/usr/bin/chown [ OK ]
/usr/bin/cp [ OK ]
/usr/bin/curl [ OK ]
/usr/bin/cut [ OK ]
/usr/bin/date [ OK ]
/usr/bin/df [ OK ]
/usr/bin/diff [ OK ]
/usr/bin/dirname [ OK ]
/usr/bin/dmesg [ OK ]
/usr/bin/du [ OK ]
/usr/bin/echo [ OK ]
/usr/bin/egrep [ Warning ]
/usr/bin/env [ OK ]
/usr/bin/fgrep [ Warning ]
/usr/bin/file [ OK ]
/usr/bin/find [ OK ]
/usr/bin/grep [ OK ]
/usr/bin/groups [ OK ]
/usr/bin/head [ OK ]
/usr/bin/id [ OK ]
/usr/bin/ipcs [ OK ]
/usr/bin/kill [ OK ]
/usr/bin/last [ OK ]
/usr/bin/lastlog [ OK ]
/usr/bin/ldd [ Warning ]
/usr/bin/less [ OK ]
/usr/bin/logger [ OK ]
/usr/bin/login [ OK ]
/usr/bin/ls [ OK ]
/usr/bin/lsattr [ OK ]
/usr/bin/md5sum [ OK ]
/usr/bin/mktemp [ OK ]
/usr/bin/more [ OK ]
/usr/bin/mount [ OK ]
/usr/bin/mv [ OK ]
/usr/bin/netstat [ OK ]
/usr/bin/newgrp [ OK ]
/usr/bin/passwd [ OK ]
/usr/bin/perl [ OK ]
/usr/bin/pgrep [ OK ]
/usr/bin/ping [ OK ]
/usr/bin/pkill [ OK ]
/usr/bin/ps [ OK ]
/usr/bin/pwd [ OK ]
/usr/bin/readlink [ OK ]
/usr/bin/rpm [ OK ]
/usr/bin/runcon [ OK ]
/usr/bin/sed [ OK ]
/usr/bin/sh [ OK ]
/usr/bin/sha1sum [ OK ]
/usr/bin/sha224sum [ OK ]
/usr/bin/sha256sum [ OK ]
/usr/bin/sha384sum [ OK ]
/usr/bin/sha512sum [ OK ]
/usr/bin/size [ OK ]
/usr/bin/sort [ OK ]
/usr/bin/ssh [ OK ]
/usr/bin/stat [ OK ]
/usr/bin/strace [ OK ]
/usr/bin/strings [ OK ]
/usr/bin/su [ OK ]
/usr/bin/sudo [ OK ]
/usr/bin/tail [ OK ]
/usr/bin/telnet [ OK ]
/usr/bin/test [ OK ]
/usr/bin/top [ OK ]
/usr/bin/touch [ OK ]
/usr/bin/tr [ OK ]
/usr/bin/uname [ OK ]
/usr/bin/uniq [ OK ]
/usr/bin/users [ OK ]
/usr/bin/vmstat [ OK ]
/usr/bin/w [ OK ]
/usr/bin/watch [ OK ]
/usr/bin/wc [ OK ]
/usr/bin/wget [ OK ]
/usr/bin/whatis [ OK ]
/usr/bin/whereis [ OK ]
/usr/bin/which [ OK ]
/usr/bin/who [ OK ]
/usr/bin/whoami [ OK ]
/usr/bin/numfmt [ OK ]
/usr/bin/kmod [ OK ]
/usr/bin/systemctl [ OK ]
/usr/bin/gawk [ OK ]
/usr/lib/systemd/systemd [ OK ]
/etc/rkhunter.conf [ OK ]
[Press <ENTER> to continue]
Checking for rootkits...
Performing check of known rootkit files and directories
55808 Trojan - Variant A [ Not found ]
ADM Worm [ Not found ]
AjaKit Rootkit [ Not found ]
Adore Rootkit [ Not found ]
aPa Kit [ Not found ]
Apache Worm [ Not found ]
Ambient (ark) Rootkit [ Not found ]
Balaur Rootkit [ Not found ]
BeastKit Rootkit [ Not found ]
beX2 Rootkit [ Not found ]
BOBKit Rootkit [ Not found ]
cb Rootkit [ Not found ]
CiNIK Worm (Slapper.B variant) [ Not found ]
Danny-Boy's Abuse Kit [ Not found ]
Devil RootKit [ Not found ]
Diamorphine LKM [ Not found ]
Dica-Kit Rootkit [ Not found ]
Dreams Rootkit [ Not found ]
Duarawkz Rootkit [ Not found ]
Ebury backdoor [ Not found ]
Enye LKM [ Not found ]
Flea Linux Rootkit [ Not found ]
Fu Rootkit [ Not found ]
Fuck`it Rootkit [ Not found ]
GasKit Rootkit [ Not found ]
Heroin LKM [ Not found ]
HjC Kit [ Not found ]
ignoKit Rootkit [ Not found ]
IntoXonia-NG Rootkit [ Not found ]
Irix Rootkit [ Not found ]
Jynx Rootkit [ Not found ]
Jynx2 Rootkit [ Not found ]
KBeast Rootkit [ Not found ]
Kitko Rootkit [ Not found ]
Knark Rootkit [ Not found ]
ld-linuxv.so Rootkit [ Not found ]
Li0n Worm [ Not found ]
Lockit / LJK2 Rootkit [ Not found ]
Mokes backdoor [ Not found ]
Mood-NT Rootkit [ Not found ]
MRK Rootkit [ Not found ]
Ni0 Rootkit [ Not found ]
Ohhara Rootkit [ Not found ]
Optic Kit (Tux) Worm [ Not found ]
Oz Rootkit [ Not found ]
Phalanx Rootkit [ Not found ]
Phalanx2 Rootkit [ Not found ]
Phalanx2 Rootkit (extended tests) [ Not found ]
Portacelo Rootkit [ Not found ]
R3dstorm Toolkit [ Not found ]
RH-Sharpe's Rootkit [ Not found ]
RSHA's Rootkit [ Not found ]
Scalper Worm [ Not found ]
Sebek LKM [ Not found ]
Shutdown Rootkit [ Not found ]
SHV4 Rootkit [ Not found ]
SHV5 Rootkit [ Not found ]
Sin Rootkit [ Not found ]
Slapper Worm [ Not found ]
Sneakin Rootkit [ Not found ]
'Spanish' Rootkit [ Not found ]
Suckit Rootkit [ Not found ]
Superkit Rootkit [ Not found ]
TBD (Telnet BackDoor) [ Not found ]
TeLeKiT Rootkit [ Not found ]
T0rn Rootkit [ Not found ]
trNkit Rootkit [ Not found ]
Trojanit Kit [ Not found ]
Tuxtendo Rootkit [ Not found ]
URK Rootkit [ Not found ]
Vampire Rootkit [ Not found ]
VcKit Rootkit [ Not found ]
Volc Rootkit [ Not found ]
Xzibit Rootkit [ Not found ]
zaRwT.KiT Rootkit [ Not found ]
ZK Rootkit [ Not found ]
[Press <ENTER> to continue]
Performing additional rootkit checks
Suckit Rootkit additional checks [ OK ]
Checking for possible rootkit files and directories [ None found ]
Checking for possible rootkit strings [ None found ]
Performing malware checks
Checking running processes for suspicious files [ None found ]
Checking for login backdoors [ None found ]
Checking for sniffer log files [ None found ]
Checking for suspicious directories [ None found ]
Checking for suspicious (large) shared memory segments [ None found ]
Checking for Apache backdoor [ Not found ]
Performing Linux specific checks
Checking loaded kernel modules [ OK ]
Checking kernel module names [ OK ]
[Press <ENTER> to continue]
Checking the network...
Performing checks on the network ports
Checking for backdoor ports [ None found ]
Performing checks on the network interfaces
Checking for promiscuous interfaces [ None found ]
Checking the local host...
Performing system boot checks
Checking for local host name [ Found ]
Checking for system startup files [ Found ]
Checking system startup files for malware [ None found ]
Performing group and account checks
Checking for passwd file [ Found ]
Checking for root equivalent (UID 0) accounts [ None found ]
Checking for passwordless accounts [ None found ]
Checking for passwd file changes [ None found ]
Checking for group file changes [ None found ]
Checking root account shell history files [ OK ]
Performing system configuration file checks
Checking for an SSH configuration file [ Found ]
Checking if SSH root access is allowed [ Warning ]
Checking if SSH protocol v1 is allowed [ Warning ]
Checking for other suspicious configuration settings [ None found ]
Checking for a running system logging daemon [ Found ]
Checking for a system logging configuration file [ Found ]
Checking if syslog remote logging is allowed [ Not allowed ]
Performing filesystem checks
Checking /dev for suspicious file types [ Warning ]
Checking for hidden files and directories [ Warning ]
[Press <ENTER> to continue]
System checks summary
=====================
File properties checks...
Required commands check failed
Files checked: 127
Suspect files: 5
Rootkit checks...
Rootkits checked : 496
Possible rootkits: 0
Applications checks...
All checks skipped
The system checks took: 5 minutes and 43 seconds
All results have been written to the log file: /var/log/rkhunter.log
One or more warnings have been found while checking the system.
Please check the log file (/var/log/rkhunter.log)
解读:每项检测结果都高亮显示,绿色表示正常,红色表示需要引起关注,上面的检测需要与用户交互输入“回车”,可以使用–sk选项使其自动检测:
[root@master rkhunter-1.4.6]# rkhunter –check –skip-keypress
3、定时检测
Linux终端使用rkhunter来检测,最大的好处在于每项的检测结果都有不同的颜色显示,如果是绿色的表示没有问题,如果是红色的,那就要引起关注了。另外,在上面执行检测的过程中,在每个部分检测完成后,需要以Enter键来继续。如果要让程序自动运行,可以执行如下命令:
30 09 * * * root /usr/local/bin/rkhunter –check –cronjob
解读:rkhunter检测程序就会在每天的9:30分运行一次。
4、安全更新
测试是否存在漏洞,执行以下命令:
$ env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
vulnerable
this is a test
如果显示如上,那么,很遗憾,必须立即打上安全补丁修复,
临时解决办法为:
yum -y update bash
升级bash后,执行测试:
$ env x='() { :;}; echo vulnerable’ bash -c “echo this is a test”
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x’
this is a test
如果显示如上,表示已经修补了漏洞。
(本文由美国主机侦探原创,转载请注明出处“美国主机侦探”和原文地址!)

微信扫码加好友进群
主机优惠码及时掌握

QQ群号:938255063
主机优惠发布与交流